
by Fronetics | Oct 29, 2015 | Blog, Leadership, Logistics, Strategy, Supply Chain
 We know that with the increasing growth of cyber-hacking and data breaches, investing in IT asset disposition (ITAD) is a growing necessity for companies. It is critical to ensure the safety of a company’s confidential live and stored data on all of its assets, ranging from computers, phones, servers, and hard drives. If breached, a company’s reputation, consumer base, finances and future viability are all at risk. What happens to data and technological gear after it is retired can be equally as critical as the current live data and in-service equipment. Proper disposal is not only important to the integrity and success of the company, its partners, and clients, but it may also protect the environment. While some sectors have strict regulations and requirements regarding ITAD, others do not, but whatever the case, the ethical obligation is huge.
We know that with the increasing growth of cyber-hacking and data breaches, investing in IT asset disposition (ITAD) is a growing necessity for companies. It is critical to ensure the safety of a company’s confidential live and stored data on all of its assets, ranging from computers, phones, servers, and hard drives. If breached, a company’s reputation, consumer base, finances and future viability are all at risk. What happens to data and technological gear after it is retired can be equally as critical as the current live data and in-service equipment. Proper disposal is not only important to the integrity and success of the company, its partners, and clients, but it may also protect the environment. While some sectors have strict regulations and requirements regarding ITAD, others do not, but whatever the case, the ethical obligation is huge.
The Cost of Hacking and Breaches
Akamai Technologies’ State of the Internet report showed that “hacker attacks on websites went up 75% in the final quarter of 2013, with hackers in China responsible for 43% of all attacks.” More recently, in 2014 the Cost of Cyber Crime Study was conducted by Ponemon and sponsored by HP. It found that crimes are more expensive, happen more frequently, and require more time to resolve than ever. It also found that crimes happened across various sectors (see below).
2014 Cost of Cyber Crime Study
- The average annualized cost of cyber crime was $12.7 million, with a range of $1.6 million to $61 million; an increase of 9 percent or $1.1 million over the average cost reported in 2013.
- There are an average of 138 successful attacks per week, compared to 50 attacks per week when the study was initially conducted in 2010.
- The average time to detect a malicious or criminal attack by a global study sample of organizations was 170 days. The longest average time segmented by type of attack was 259 days, and involved incidents concerning malicious insiders. The average time to resolve a cyber attack once detected was 45 days, while the average cost incurred during this period was $1,593,627 – representing a 33-percent increase over last year’s estimated average cost of $1,035,769 for a 32-day period.
ITAD: A Growing Business
According to TMR as reported in IT: Connect and Expand, the ITAD market will expand to $41 billion by 2019 on 141 million tons of used equipment. With the heavy responsibility that goes with ITAD in terms of proper wiping, disposal, reusing and recycling, more companies are working with 3rd-party service providers who specialize in ITAD. According to Business Wire 65 percent of companies larger than 10,000 workers, and up to one third of all businesses, are turning to 3rd-party service providers to manage end-of-life assets.
What if something goes wrong?
It makes sense with the increase of cyber crime that there would be cyber insurance. This may be one solution to protect yourself, however, according to observations made on the site Dark Reading, “cookie-cutter” cyber insurance might not be everything you need.
This post originally appeared on Electronics Purchasing Strategies.
You may also like:

by Fronetics | Oct 28, 2015 | Blog, Consumer Electronics, Data Security, Data/Analytics, Logistics, Strategy, Supply Chain

When it comes to IT Asset Disposal here are 5 must-ask questions for third-party providers.
When the industry thinks of data breaches it raises the specter of a savvy hacker lurking very far, and yet very close, intermingling with a larger organization of internet criminals, breaking into our technology and gathering most private information: credit card and bank account details, social security numbers, and personal health and income data. The recent breaches at Anthem insurance and the retail giant Target make users worry about the trail they leave when they swipe a card or populate a form with personal information. This is how individuals think identities might be exposed. Individuals often don’t think about what happens when a company retires old servers, computers, printers, copiers, and scanners. What happens to confidential data? This is something businesses must think about.
ITAD
Receipt, processing, destruction and disposal of hardware and software are a necessary and growing business. The Blumberg Advisory Group’s 2014 ITAD Trends Report shows that data security is the number one reason why companies implement an IT asset disposition (ITAD) strategy. News reports highlight examples of sensitive data being found on retired assets, frompersonal photos and information to matters of national security. The costs associated with data breaches and with the improper disposal of IT assets are great. They include financial implications such as penalties, the loss of customer loyalty, and the tarnishing of one’s reputation. To mitigate risk, asset recovery management is critical to companies operating in today’s global supply chain.
According to Transparency Market Research (TMR) as reported inElectronics Purchasing Strategies, ITAD represents an estimated $9.8 billion handling 48 million tons of discontinued or excess technology gear. According to TMR, by 2019 the predicted market will grow to $41 billion made on 141 million tons of used equipment. Concerns about data security have resulted in companies becoming more aware of the need for ITAD and the need to budget for it. In 2014, 87 percent of companies reported having an ITAD budget; 38 percent more than in 2012.
Outsourcing this complex work can be a necessity for many companies who don’t understand the intricacies, regulations, labor and cost of asset disposition. Electronically stored data is subject to stringent HIPAA/HITECH, FACTA, SOX, GLB, and FERPA regulations, complicating responsible disposal. Secure and thorough “wiping” of data is critical, and the environmental impact of retired assets is also a vital concern.
More and more companies, 65 percent of companies larger than 10,000 workers and up to one third of all businesses, are turning to 3rd-party service providers to manage end-of-life assets. The factors seen as most important in selecting a 3rd-party service provider include: adoption of industry-recognized compliance standards (97 percent); a well-documented and enforced chain of custody (95 percent); and high-quality, thorough client reporting (95 percent).
Reduce, Reuse, Recycle
ITAD is expensive and it can be risky. It is, therefore, important to find a 3rd-party service provider who can ensure as much safety and security as possible. Many ITAD companies have a split business model working with upstream partners to collect and process retired material, then turning to downstream partners who are looking to purchase used technology gear. Given this model, your server could be someone else’s server one day. Ensuring proper receipt and processing is critical.
Must-Ask Questions
These are must-ask questions businesses should ask 3rd-party providers before hiring them. Be certain these questions are answered thoroughly and confidently.
1. What is your specialization?
2. Is there uniformity in the process?
3. Who would manage our relationship?
4. How flexible are your operations?
5. What if something goes wrong?
Companies operating in today’s global supply chain need to take the necessary steps to mitigate risk when it comes to asset recovery management.
You may also like:
The importance of Asset Recovery Management in the Global Supply Chain
Content marketing ROI for reverse logistics companies
This article was originally published on Electronics Purchasing Strategies.
by Fronetics | Mar 24, 2015 | Blog, Strategy, Supply Chain

The Blumberg Advisory Group’s 2014 ITAD Trends Report shows that data security is the number one reason why companies implement an IT asset disposition (ITAD) strategy. That companies are concerned about data security is no surprise. Ongoing media reports have not only focused on data breaches, but have also highlighted examples of sensitive data being found on retired assets. The costs associated with data breaches and with the improper disposal of IT assets are great. They include financial implications such as penalties as well as the loss of customer loyalty and reputation. To mitigate risk, asset recovery management is critical to companies operating in today’s global supply chain.
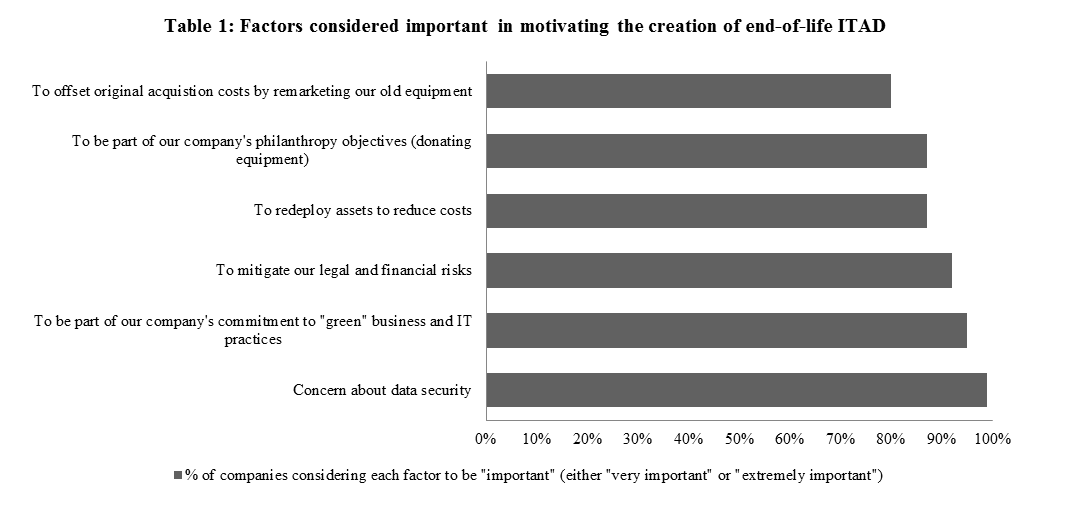
Data security is viewed as an important piece of asset recovery management
Ninety-nine percent of companies surveyed by the Blumberg Advisory Group reported that “concern about data security” is either “very important” or “extremely important” with respect to motivating the creation of their current end-of-life IT disposition strategy. Other important factors include: commitment to “Green” businesses and IT practices, mitigating legal and financial risks, and redeploying assets to reduce costs (Table 1).
Concerns about data security have resulted in companies becoming more aware of the need for ITAD and the need to budget for it. In 2014 87 percent of companies reported having an ITAD budget; 38 percent more than in 2012.
Companies turn to 3rd-party service providers
The majority (63 percent) of companies reported that they use a 3rd-party service provider to manage end-of-life assets. The factors seen as most important in selecting a 3rd-party service provider include: adoption of industry-recognized compliance standards (97 percent); a well-documented and enforced chain of custody (95 percent); and high-quality, thorough client reporting (95 percent).
What to look for in a 3rd-party service provider
ITAD is expensive and it can be risky. It is therefore important to find a 3rd-party service provider who can provide as much safety and security as possible. It is also important to find a provider that takes the time to understand your business and your needs – and develops and manages an asset recovery program that is right for you rather than one that is “out of the box.”
We have put together a list of five must-ask questions. These are questions you should ask providers with whom your company is considering engaging. Before engaging, make sure that you are given answers to these questions and that you feel confident with responses.
-
What is your specialization?
3rd-party service providers are becoming increasingly specialized, particularly when comes to corporate IT take-outs. This specialization is largely being driven by data security and data breach concerns. If your company has highly specialized assets it is essential to determine what specializations, if any, the provider has.
-
Is there uniformity in the process?
Does the provider operate on a single global platform, or will it be necessary to use different platforms for different regions of operation. Uniformity in the process generally increases the ease of operation and ease of use.
-
Who would manage our relationship?
Would the provider assign one global account manager, or will it be necessary to interface with several account managers? Again, this boils down to ease of operation and ease of use.
-
How flexible are your operations?
Disruptions such as recent closure of west coast ports, natural disasters such as Hurricane Sandy, and changing standards and regulations (on a local, regional, and global scale) all impact the supply chain. Given this, it is important that flexibility be a component of asset recovery management.
-
What if something goes wrong?
This question is the most important question to ask. If something goes wrong and if ITAD does not occur as it should, what happens? Does the provider carry indemnification? If so, how much does the provider carry? Will the provider work with you to mitigate risk?
Data security, data breaches, and the improper disposal of assets are issues which global supply chain companies face on a day to day basis. The economic and social implications of the mismanagement of asset recovery are great. It is therefore important that companies operating in today’s global supply chain take the necessary steps to mitigate risk when it comes to asset recovery management.

by Fronetics | Mar 24, 2015 | Blog, Strategy, Supply Chain

The Blumberg Advisory Group’s 2014 ITAD Trends Report shows that data security is the number one reason why companies implement an IT asset disposition (ITAD) strategy. That companies are concerned about data security is no surprise. Ongoing media reports have not only focused on data breaches, but have also highlighted examples of sensitive data being found on retired assets. The costs associated with data breaches and with the improper disposal of IT assets are great. They include financial implications such as penalties as well as the loss of customer loyalty and reputation. To mitigate risk, asset recovery management is critical to companies operating in today’s global supply chain.
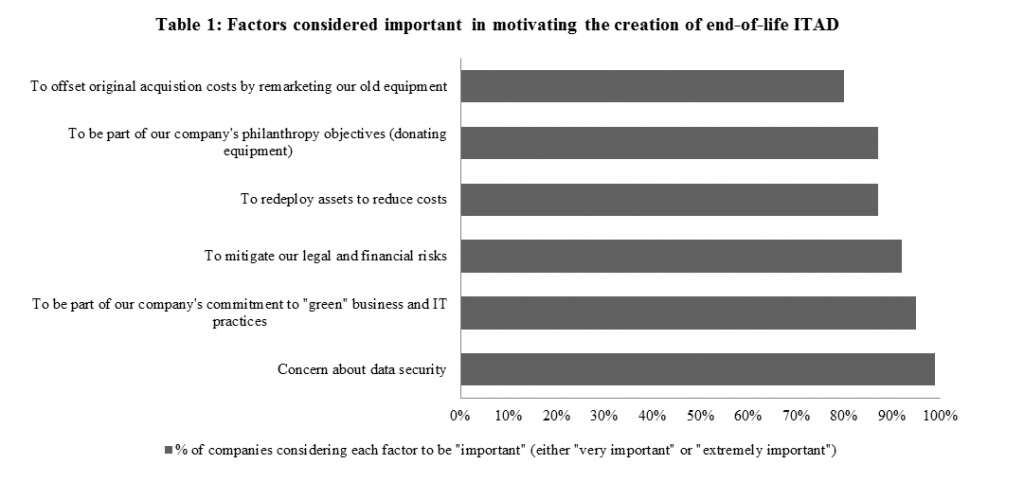
Data security is viewed as an important piece of asset recovery management
Ninety-nine percent of companies surveyed by the Blumberg Advisory Group reported that “concern about data security” is either “very important” or “extremely important” with respect to motivating the creation of their current end-of-life IT disposition strategy. Other important factors include: commitment to “Green” businesses and IT practices, mitigating legal and financial risks, and redeploying assets to reduce costs (Table 1).

Concerns about data security have resulted in companies becoming more aware of the need for ITAD and the need to budget for it. In 2014 87 percent of companies reported having an ITAD budget; 38 percent more than in 2012.
Companies turn to 3rd-party service providers
The majority (63 percent) of companies reported that they use a 3rd-party service provider to manage end-of-life assets. The factors seen as most important in selecting a 3rd-party service provider include: adoption of industry-recognized compliance standards (97 percent); a well-documented and enforced chain of custody (95 percent); and high-quality, thorough client reporting (95 percent).
What to look for in a 3rd-party service provider
ITAD is expensive and it can be risky. It is therefore important to find a 3rd-party service provider who can provide as much safety and security as possible. It is also important to find a provider that takes the time to understand your business and your needs – and develops and manages an asset recovery program that is right for you rather than one that is “out of the box.”
We have put together a list of five must-ask questions. These are questions you should ask providers with whom your company is considering engaging. Before engaging, make sure that you are given answers to these questions and that you feel confident with responses.
-
What is your specialization?
3rd-party service providers are becoming increasingly specialized, particularly when comes to corporate IT take-outs. This specialization is largely being driven by data security and data breach concerns. If your company has highly specialized assets it is essential to determine what specializations, if any, the provider has.
-
Is there uniformity in the process?
Does the provider operate on a single global platform, or will it be necessary to use different platforms for different regions of operation. Uniformity in the process generally increases the ease of operation and ease of use.
-
Who would manage our relationship?
Would the provider assign one global account manager, or will it be necessary to interface with several account managers? Again, this boils down to ease of operation and ease of use.
-
How flexible are your operations?
Disruptions such as recent closure of west coast ports, natural disasters such as Hurricane Sandy, and changing standards and regulations (on a local, regional, and global scale) all impact the supply chain. Given this, it is important that flexibility be a component of asset recovery management.
-
What if something goes wrong?
This question is the most important question to ask. If something goes wrong and if ITAD does not occur as it should, what happens? Does the provider carry indemnification? If so, how much does the provider carry? Will the provider work with you to mitigate risk?
Data security, data breaches, and the improper disposal of assets are issues which global supply chain companies face on a day to day basis. The economic and social implications of the mismanagement of asset recovery are great. It is therefore important that companies operating in today’s global supply chain take the necessary steps to mitigate risk when it comes to asset recovery management.

 We know that with the increasing growth of cyber-hacking and data breaches, investing in IT asset disposition (ITAD) is a growing necessity for companies. It is critical to ensure the safety of a company’s confidential live and stored data on all of its assets, ranging from computers, phones, servers, and hard drives. If breached, a company’s reputation, consumer base, finances and future viability are all at risk. What happens to data and technological gear after it is retired can be equally as critical as the current live data and in-service equipment. Proper disposal is not only important to the integrity and success of the company, its partners, and clients, but it may also protect the environment. While some sectors have strict regulations and requirements regarding ITAD, others do not, but whatever the case, the ethical obligation is huge.
We know that with the increasing growth of cyber-hacking and data breaches, investing in IT asset disposition (ITAD) is a growing necessity for companies. It is critical to ensure the safety of a company’s confidential live and stored data on all of its assets, ranging from computers, phones, servers, and hard drives. If breached, a company’s reputation, consumer base, finances and future viability are all at risk. What happens to data and technological gear after it is retired can be equally as critical as the current live data and in-service equipment. Proper disposal is not only important to the integrity and success of the company, its partners, and clients, but it may also protect the environment. While some sectors have strict regulations and requirements regarding ITAD, others do not, but whatever the case, the ethical obligation is huge.




