
by Fronetics | Sep 22, 2015 | Blog, Logistics, Strategy, Supply Chain

The perception of the reverse logistics industry has shifted over the last several years. Reverse logistics has gone from being viewed as an afterthought to a necessary evil to being recognized as a wealth of opportunity. This shift has occurred as a result of several factors including: shortened product lifecycles, increased regulations and standards, consumer demand for corporate responsibility, and an increase in razor-thin margins. Equally important in the industry’s makeover – companies have come to understand and to realize the benefits of reverse logistics such as a reduction in costs, a revenue stream, and as a way to enhance customer loyalty.
Unfortunately when choosing a solutions provider, many companies fall prey to the assumption that a certain level of compliance and data security are givens. More often than not; however, the reality is that the service provider does not offer the level of compliance or data security assumed by the customer – and more often than not, the level that is offered by the service provider is inadequate. When due diligence is left to assumptions companies pay dearly.
Specifically, faulty assumptions regarding certain levels of compliance and data security provided via a service provider leave the customer open to lawsuits and fines as a result of non-compliance and leave the door open for data leakage and theft. The financial costs associated can be astronomical. Moreover, the company and the brand can take a significant hit resulting in a decline or even loss of customers and customer loyalty. In short, choosing a reverse logistics service provider that does not offer the compliance and data security necessary for your company can negate any gains realized as a result of your company’s reverse logistics strategy.
When selecting a reverse logistics service provider don’t make assumptions; don’t take the route of complacency. Instead, ask questions, conduct due diligence, and make sure that the level of service provided goes beyond meeting your needs – the service provider should be able to exceed your company’s needs.
When selecting a reverse logistics service provider, look for a provider who has network and standards in place which ensure global success. What does this look like? Arrow Value Recovery is the gold standard. Arrow provides uniform standards and quality controls. Unlike some service providers who default to the lowest common denominator, Arrow providers customers with consistent levels of service –globally. Moreover, Arrow ensures that every step of the recovery, data sanitization, and reuse and recycling process is not only transparent but is also 100 percent auditable.
Taking the time to thoroughly vet a reverse logistics service provider is essential. Don’t make assumptions and don’t default to complacency. Did you know that an estimated 70 percent of data breaches come from computers that are offline – typically computers that have been disposed of by the equipment owner? Don’t assume that your reverse logistics provider is offering your company the level of compliance and data security necessary – verify the facts.
This post was originally published on Electronics Purchasing Strategies.

by Fronetics | Aug 4, 2015 | Blog, Content Marketing, Logistics, Marketing, Supply Chain

Do reverse logistics companies need to focus on content marketing? Yes.
Should they use LinkedIn? Yes. Twitter? Yes. YouTube? Yes. Yes. Yes. Should they blog? Yes!
Several reverse logistics companies are already using content marketing in an effort to connect with peers and potential B2B consumers. IT Asset Disposal (ITAD) company, TradePort, has an informative blog and utilizes LinkedIn, Facebook, and Twitter. The large 3rd-party logistics (3PL) company, Unyson, utilizes the top B2B social media outlets with just under 2,000 followers on Twitter and just over 3,000 followers on LinkedIn. On the homepage of their website you can view a running tally of how much money they have saved their customers. At the time of the writing of this blog it’s at $2,055,763,398.
What the studies show:
The Content Marketing Institute reports that 8 out of 10 people identify themselves as blog readers, and 23% of all time spent online is spent on social media sites. With the rise of the blog, companies have gotten smart about how to reach their current and potential consumers. According to Forbes, many brands are moving their advertising budgets from television to online videos.
In the B2B world things are changing, too, with many executives wanting to gain information through other mediums. The Content Marketing Institute also reports that a majority (80%) of business decision-makers prefer to get information from articles rather than through advertisements.
We know that inbound marketing is effective in garnering consumers’ attention. It’s aligned with a generation of people who want to be educated about the products they’re buying and who are willing to search for those products online. Even with all of this known, it’s important to ask: what is the ROI when it comes to content marketing?
Return on Investment
In order to calculate ROI, the cost of content marketing needs to be assessed:
- salaries (if going in-house)
- marketing agency or contractor services
- additional overhead
- distribution costs
- design and publication software
After those costs have been calculated, the next step is to subtract that number from the revenue generated. The Guardian has put forth its simple content marketing ROI calculator:
(Revenue Generated – Cost of Content Marketing) / Cost of Content Marketing = ROI
According to the newspaper, “A simple calculation could say that you drove 1000 visits through a piece of content, and Google Ads would have cost £1 per click, e.g. £1000 to equal the same. If the content only cost £500, you have a saving!”
But with most seemingly simple things, there’s complexity underneath. Dig deeper and ask more questions:
- Is the money you’re spending on inbound marketing deterring other, less obvious, costs?
- Would it have cost you more through outbound marketing methods to achieve that same level of visibility than through inbound marketing solutions?
- Is inbound marketing bringing in customers or closing a deal more quickly than alternative methods (time is money, after all)?
- Is inbound marketing cutting down the need for staffing in other areas, such as support staff to manage inquiries or support calls?
Some incalculable values from inbound marketing, like consumer preferences, content intelligence, customer relationship strategies, and branding can be hard to tie to a number, but over time you will see that your ROI will become more clear to you as you generate leads, turn leads into customers, and see the result in the form of money gained (American dollars or British pounds!).
There are several ways to measure ROI. Reverse logistics will continue to grow in importance as regulations increase and the environment continues to come to the forefront as an ethical and practical issue. Content is king, so consider it, measure it, and go for it.
Fronetics Strategic Advisors is a leading management consulting firm. Our firm works with companies to identify and execute strategies for growth and value creation.
When it comes to marketing we work with our clients to create and execute strategies that drive success and elevate their brand position within the industry. Unlike other firms, we align marketing programs with business objectives and, through a data driven approach, are able to deliver results with a targeted ROI. Our team is comprised of strategists, marketing professionals, writers, designers, and experts in social media. Together we leverage our experience to increase brand awareness, position our clients as thought leaders, drive meaningful engagement with prospects and customers, and help businesses grow.

by Fronetics | Mar 24, 2015 | Blog, Strategy, Supply Chain

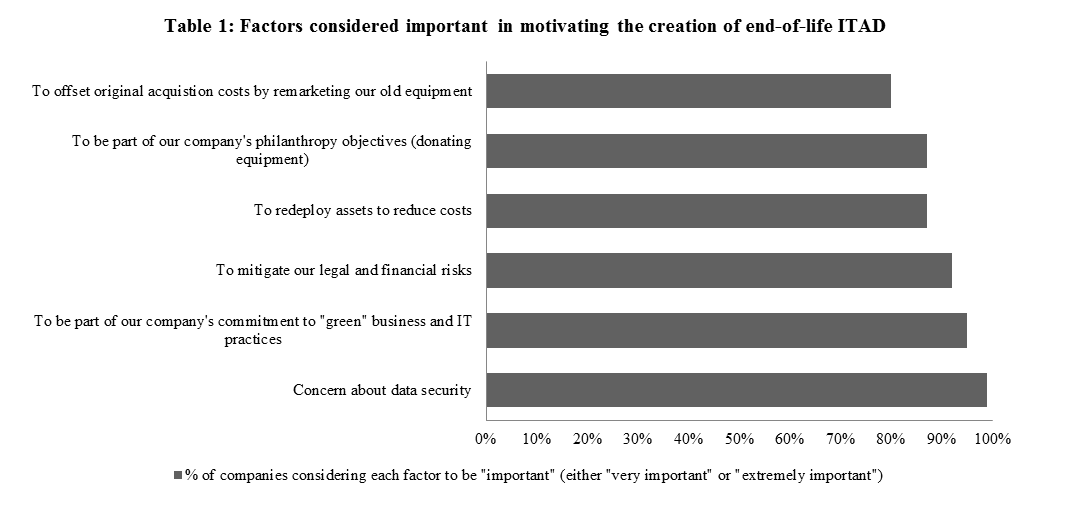
The Blumberg Advisory Group’s 2014 ITAD Trends Report shows that data security is the number one reason why companies implement an IT asset disposition (ITAD) strategy. That companies are concerned about data security is no surprise. Ongoing media reports have not only focused on data breaches, but have also highlighted examples of sensitive data being found on retired assets. The costs associated with data breaches and with the improper disposal of IT assets are great. They include financial implications such as penalties as well as the loss of customer loyalty and reputation. To mitigate risk, asset recovery management is critical to companies operating in today’s global supply chain.
Data security is viewed as an important piece of asset recovery management
Ninety-nine percent of companies surveyed by the Blumberg Advisory Group reported that “concern about data security” is either “very important” or “extremely important” with respect to motivating the creation of their current end-of-life IT disposition strategy. Other important factors include: commitment to “Green” businesses and IT practices, mitigating legal and financial risks, and redeploying assets to reduce costs (Table 1).
Concerns about data security have resulted in companies becoming more aware of the need for ITAD and the need to budget for it. In 2014 87 percent of companies reported having an ITAD budget; 38 percent more than in 2012.
Companies turn to 3rd-party service providers
The majority (63 percent) of companies reported that they use a 3rd-party service provider to manage end-of-life assets. The factors seen as most important in selecting a 3rd-party service provider include: adoption of industry-recognized compliance standards (97 percent); a well-documented and enforced chain of custody (95 percent); and high-quality, thorough client reporting (95 percent).
What to look for in a 3rd-party service provider
ITAD is expensive and it can be risky. It is therefore important to find a 3rd-party service provider who can provide as much safety and security as possible. It is also important to find a provider that takes the time to understand your business and your needs – and develops and manages an asset recovery program that is right for you rather than one that is “out of the box.”
We have put together a list of five must-ask questions. These are questions you should ask providers with whom your company is considering engaging. Before engaging, make sure that you are given answers to these questions and that you feel confident with responses.
-
What is your specialization?
3rd-party service providers are becoming increasingly specialized, particularly when comes to corporate IT take-outs. This specialization is largely being driven by data security and data breach concerns. If your company has highly specialized assets it is essential to determine what specializations, if any, the provider has.
-
Is there uniformity in the process?
Does the provider operate on a single global platform, or will it be necessary to use different platforms for different regions of operation. Uniformity in the process generally increases the ease of operation and ease of use.
-
Who would manage our relationship?
Would the provider assign one global account manager, or will it be necessary to interface with several account managers? Again, this boils down to ease of operation and ease of use.
-
How flexible are your operations?
Disruptions such as recent closure of west coast ports, natural disasters such as Hurricane Sandy, and changing standards and regulations (on a local, regional, and global scale) all impact the supply chain. Given this, it is important that flexibility be a component of asset recovery management.
-
What if something goes wrong?
This question is the most important question to ask. If something goes wrong and if ITAD does not occur as it should, what happens? Does the provider carry indemnification? If so, how much does the provider carry? Will the provider work with you to mitigate risk?
Data security, data breaches, and the improper disposal of assets are issues which global supply chain companies face on a day to day basis. The economic and social implications of the mismanagement of asset recovery are great. It is therefore important that companies operating in today’s global supply chain take the necessary steps to mitigate risk when it comes to asset recovery management.

by Fronetics | Mar 24, 2015 | Blog, Strategy, Supply Chain

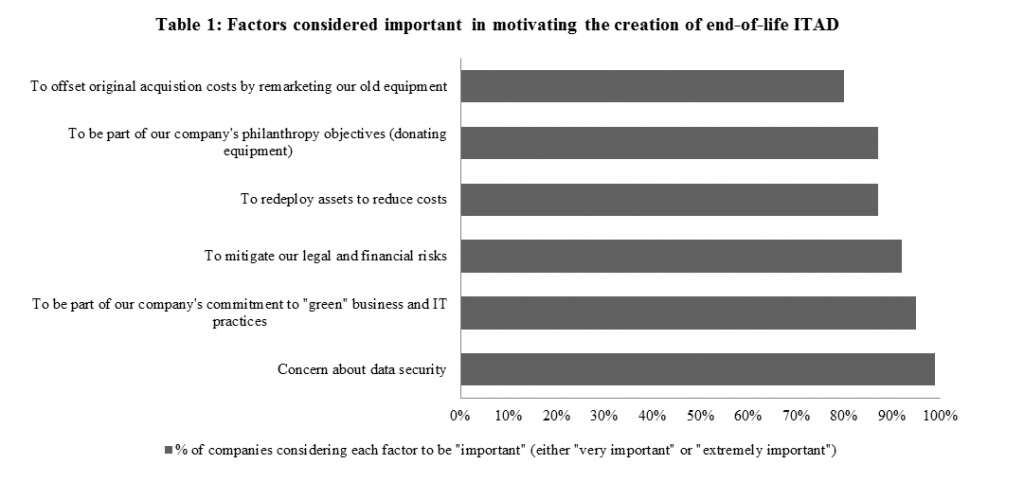
The Blumberg Advisory Group’s 2014 ITAD Trends Report shows that data security is the number one reason why companies implement an IT asset disposition (ITAD) strategy. That companies are concerned about data security is no surprise. Ongoing media reports have not only focused on data breaches, but have also highlighted examples of sensitive data being found on retired assets. The costs associated with data breaches and with the improper disposal of IT assets are great. They include financial implications such as penalties as well as the loss of customer loyalty and reputation. To mitigate risk, asset recovery management is critical to companies operating in today’s global supply chain.
Data security is viewed as an important piece of asset recovery management
Ninety-nine percent of companies surveyed by the Blumberg Advisory Group reported that “concern about data security” is either “very important” or “extremely important” with respect to motivating the creation of their current end-of-life IT disposition strategy. Other important factors include: commitment to “Green” businesses and IT practices, mitigating legal and financial risks, and redeploying assets to reduce costs (Table 1).

Concerns about data security have resulted in companies becoming more aware of the need for ITAD and the need to budget for it. In 2014 87 percent of companies reported having an ITAD budget; 38 percent more than in 2012.
Companies turn to 3rd-party service providers
The majority (63 percent) of companies reported that they use a 3rd-party service provider to manage end-of-life assets. The factors seen as most important in selecting a 3rd-party service provider include: adoption of industry-recognized compliance standards (97 percent); a well-documented and enforced chain of custody (95 percent); and high-quality, thorough client reporting (95 percent).
What to look for in a 3rd-party service provider
ITAD is expensive and it can be risky. It is therefore important to find a 3rd-party service provider who can provide as much safety and security as possible. It is also important to find a provider that takes the time to understand your business and your needs – and develops and manages an asset recovery program that is right for you rather than one that is “out of the box.”
We have put together a list of five must-ask questions. These are questions you should ask providers with whom your company is considering engaging. Before engaging, make sure that you are given answers to these questions and that you feel confident with responses.
-
What is your specialization?
3rd-party service providers are becoming increasingly specialized, particularly when comes to corporate IT take-outs. This specialization is largely being driven by data security and data breach concerns. If your company has highly specialized assets it is essential to determine what specializations, if any, the provider has.
-
Is there uniformity in the process?
Does the provider operate on a single global platform, or will it be necessary to use different platforms for different regions of operation. Uniformity in the process generally increases the ease of operation and ease of use.
-
Who would manage our relationship?
Would the provider assign one global account manager, or will it be necessary to interface with several account managers? Again, this boils down to ease of operation and ease of use.
-
How flexible are your operations?
Disruptions such as recent closure of west coast ports, natural disasters such as Hurricane Sandy, and changing standards and regulations (on a local, regional, and global scale) all impact the supply chain. Given this, it is important that flexibility be a component of asset recovery management.
-
What if something goes wrong?
This question is the most important question to ask. If something goes wrong and if ITAD does not occur as it should, what happens? Does the provider carry indemnification? If so, how much does the provider carry? Will the provider work with you to mitigate risk?
Data security, data breaches, and the improper disposal of assets are issues which global supply chain companies face on a day to day basis. The economic and social implications of the mismanagement of asset recovery are great. It is therefore important that companies operating in today’s global supply chain take the necessary steps to mitigate risk when it comes to asset recovery management.

by Elizabeth Hines | Nov 12, 2013 | Blog, Leadership, Strategy

Source: www.Chickenmaker.net
A 2013 study conducted by Deloitte found that 64 percent of the global executives surveyed reported they had a risk management program in place that is specific to the supply chain. That being said, 45 percent of the respondents said their programs were somewhat effective or not effective at all. Respondents — especially those in the technology, industrial products, and diversified manufacturing sectors — reported that supply chain disruptions have become more costly over the past three years. They also cited margin erosion and sudden demand change as two of the most costly problems. Moreover, the 2013 Global Supply Chain and Risk Management Survey conducted by the MIT Forum for Supply Innovation and PricewaterhouseCoopers found that in the last 12 months more than 60 percent of companies surveyed reported that their performance indicators had dropped by more than three percent due to supply chain disruptions. While there are many factors which are likely to contribute to the issues pointed to in these studies, I believe that one is that companies focus largely developing risk management strategies to mitigate and cope cataclysmic events and not the day-to-day bumps in the road. As such, companies tend to be ill-prepared to handle the day-to-day bumps.
Big events are outlier events
Because big events such as hurricanes, tornados, tsunamis, and terrorist attacks can have a long-lasting impact and often visual impact on the logistics and supply chain industries they tend to stay top of mind. That being said, these events are outlier events. “Outlier events have much more influence than they should,” Professor Ananth Raman of Harvard Business School told David Stauffer for an article for the school’s website. M. Eric Johnson, director of the Center for Digital Strategies at Dartmouth College’s Tuck School of Business, told Stauffer for the same article, “Managers will often consider the giant risk but ignore the smaller risks that create friction in the supply chain.” When companies ignore the smaller risks, they do so at their peril.
You can’t ignore the day-to-day
Creating risk management strategies that focus on the everyday events is critical. Dealing with these events in a reactive and piecemeal fashion is inefficient and ineffective and can significantly hurt your company. The following are some tips on what to consider when developing an effective risk management strategy which focuses on the everyday risks:
- Employ a strategy that is robust and closely monitored.
- Put a leader in charge.
- Clearly define your process and make it comprehensive. Establish a well-defined process to mitigate events such as cashflow contingencies, client credit risk and default, competitor interruptions, inventory risk, data backup and recovery, key client attrition, employee satisfaction and retention, social media use and abuse, and reputation recovery.
- Make sure the strategy is both nimble and flexible. Being intractable can exacerbate issues.
- Don’t forget about human resources. Don’t be afraid to move employees into new roles. Moving an employee into a new role permanently (or for a specified period to deal with an event) is a powerful and effective strategy.
- Be first. If there is a problem, be sure that the clients hear about the problem from you. When you contact clients, tell them what the issue is and what you are doing to address it. Be clear, concise, and honest.
- Educate. Take the time to make sure everyone is educated about the strategy. If just one person knows the strategy, it will not be effective.
A big event might happen, but everyday events will happen… every day. Don’t give your company Chicken Little syndrome by focusing only on big events.








