
by Fronetics | Nov 5, 2015 | Blog, Content Marketing, Data/Analytics, Leadership, Marketing, Strategy

We all want to see the fruits of our labors. Whether launching a product or a new social media campaign, we look for instantaneous numbers that will affirm we made the right choices. But here’s the problem: not all metrics are created equal.
So-called vanity metrics are measurements that have no bearing on your bottom line but can give you an inflated sense of success. Generally, they are easy to calculate but are influenced by too many factors—and are too vulnerable to random external events—to be reliable.
Website visits and number of subscribers are two classic examples. A spike in homepage hits may be the result of your marketing efforts, or it may be because of ghost spam. (Or, both.) Regardless, more visits do not necessarily correlate to increased revenue—just more visits. In the same vein, having 100,000 email subscribers means nothing if only 1% are opening them. You actually could be losing money in terms of resources allocated if the emails aren’t helping drive sales.
That’s why it is crucial to focus on return on investment instead of vanity metrics. You could waste hours reviewing a hundred different analytics that tell you nothing about how revenue was affected by a particular effort. Or, worse, you could use vanity metrics to justify decisions that don’t achieve their ROI.
As a simplified example: say you spend $100 on a banner ad for a new product on an industry conference website, and your analytics report that 100 people clicked through. This sounds like success! But don’t celebrate just yet. When you dig past the vanity metric, you find an extremely high bounce rate. That means most of those click-throughs left your site immediately, neither engaging with your brand nor moving any closer to becoming a customer. In fact, you find that only one click-through converts. Was it worth paying $100 for this one customer? Probably not.
But say you ran another $100 banner ad on an industry publication website, one that targets a younger audience than you think your product fits. Only 20 visitors clicked-through, which sounds less successful than the other ad. But when you follow those 20 click-throughs down the sales funnel, you see that 15 ended up purchasing $1500 worth of product. Already, the ad has paid for itself 15 times over. You’ve also learned that perhaps a younger audience is more suited to this product. The ROI proves the vanity metric was quite misleading in this case.
Lean-startup pioneer Eric Reis, who coined the term vanity metrics, said, “The only metrics that entrepreneurs should invest energy in collecting are those that help them make decisions.” In other words, measure the things that will tell you if an effort was profitable so you know where to put your time and money.
While vanity metrics tell you nothing about your bottom line, ROI can help you determine whether it was worth spending your resources in a particular way. This is extremely useful on platforms like blogs and social media, where things are constantly changing. Using ROI as a litmus test, you can keep experimenting and making sure you’re using these tools effectively. Tracking a vanity metric like number of followers, which is likely to build over time regardless, gives you no indication of which experiments were successful and which weren’t.
Your resources are limited, so it’s crucial to evaluate your efforts with meaningful numbers that illustrate their effect on your bottom line. Calculating ROI might take some time—both in the few extra minutes to do the math and the amount of time that needs to pass before all the data is available—but that number will be infinitely more valuable to you than any vanity metric on your Google Analytics report.
What metrics do you report to your team?
Related posts:
When it comes to marketing we work with our clients to create and execute strategies that drive success and elevate their brand position within the industry. Unlike other firms, we align marketing programs with business objectives and, through a data driven approach, are able to deliver results with a targeted ROI. Our team is comprised of strategists, marketing professionals, writers, designers, and experts in social media. Together we leverage our experience to increase brand awareness, position our clients as thought leaders, drive meaningful engagement with prospects and customers, and help businesses grow. Learn more

by Fronetics | Oct 28, 2015 | Blog, Consumer Electronics, Data Security, Data/Analytics, Logistics, Strategy, Supply Chain

When it comes to IT Asset Disposal here are 5 must-ask questions for third-party providers.
When the industry thinks of data breaches it raises the specter of a savvy hacker lurking very far, and yet very close, intermingling with a larger organization of internet criminals, breaking into our technology and gathering most private information: credit card and bank account details, social security numbers, and personal health and income data. The recent breaches at Anthem insurance and the retail giant Target make users worry about the trail they leave when they swipe a card or populate a form with personal information. This is how individuals think identities might be exposed. Individuals often don’t think about what happens when a company retires old servers, computers, printers, copiers, and scanners. What happens to confidential data? This is something businesses must think about.
ITAD
Receipt, processing, destruction and disposal of hardware and software are a necessary and growing business. The Blumberg Advisory Group’s 2014 ITAD Trends Report shows that data security is the number one reason why companies implement an IT asset disposition (ITAD) strategy. News reports highlight examples of sensitive data being found on retired assets, frompersonal photos and information to matters of national security. The costs associated with data breaches and with the improper disposal of IT assets are great. They include financial implications such as penalties, the loss of customer loyalty, and the tarnishing of one’s reputation. To mitigate risk, asset recovery management is critical to companies operating in today’s global supply chain.
According to Transparency Market Research (TMR) as reported inElectronics Purchasing Strategies, ITAD represents an estimated $9.8 billion handling 48 million tons of discontinued or excess technology gear. According to TMR, by 2019 the predicted market will grow to $41 billion made on 141 million tons of used equipment. Concerns about data security have resulted in companies becoming more aware of the need for ITAD and the need to budget for it. In 2014, 87 percent of companies reported having an ITAD budget; 38 percent more than in 2012.
Outsourcing this complex work can be a necessity for many companies who don’t understand the intricacies, regulations, labor and cost of asset disposition. Electronically stored data is subject to stringent HIPAA/HITECH, FACTA, SOX, GLB, and FERPA regulations, complicating responsible disposal. Secure and thorough “wiping” of data is critical, and the environmental impact of retired assets is also a vital concern.
More and more companies, 65 percent of companies larger than 10,000 workers and up to one third of all businesses, are turning to 3rd-party service providers to manage end-of-life assets. The factors seen as most important in selecting a 3rd-party service provider include: adoption of industry-recognized compliance standards (97 percent); a well-documented and enforced chain of custody (95 percent); and high-quality, thorough client reporting (95 percent).
Reduce, Reuse, Recycle
ITAD is expensive and it can be risky. It is, therefore, important to find a 3rd-party service provider who can ensure as much safety and security as possible. Many ITAD companies have a split business model working with upstream partners to collect and process retired material, then turning to downstream partners who are looking to purchase used technology gear. Given this model, your server could be someone else’s server one day. Ensuring proper receipt and processing is critical.
Must-Ask Questions
These are must-ask questions businesses should ask 3rd-party providers before hiring them. Be certain these questions are answered thoroughly and confidently.
1. What is your specialization?
2. Is there uniformity in the process?
3. Who would manage our relationship?
4. How flexible are your operations?
5. What if something goes wrong?
Companies operating in today’s global supply chain need to take the necessary steps to mitigate risk when it comes to asset recovery management.
You may also like:
The importance of Asset Recovery Management in the Global Supply Chain
Content marketing ROI for reverse logistics companies
This article was originally published on Electronics Purchasing Strategies.
![Supply Chain: 4 Essential Year End Questions to Ask Yourself [Infographic]](https://fronetics.com/wp-content/uploads/2024/10/supply-chain-year-end-questions-900x675.jpg)
by Fronetics | Oct 27, 2015 | Blog, Data/Analytics, Leadership, Strategy, Supply Chain

As the new year approaches, don’t overlook the valuable information you can glean from conducting a year-end review.
Don’t start the new year without asking these 4 essential questions.
What were my biggest accomplishments this year?
Twelve months can seem like a long time when you consider everything that happened over the course of the last 365 days. Setting aside some time to review successful projects, notes of thanks from clients, or a particularly positive performance review reminds us what we’re capable of achieving and gives us a renewed sense of accomplishment.
Try this: Designate a file folder near your workspace to collect any materials or notes related to your successes as they occur. Doing so will make it easier for you to recall your accomplishments and provide quick access to a list of your achievements – helpful for a healthy dose of motivation or last-minute performance reviews.
How satisfied are you with the past year?
Were you successful in meeting the majority of your goals? Do you feel that you worked to your highest potential? Would you have done something differently? What about missed opportunities? Examining what went right and identifying areas for growth and opportunity are powerful exercises that both prevent the recurrence of negative behaviors and reinforce our commitment to priorities.
Try this: Thinking about your experiences of the past year in sum, try to assign a value to your entire year. How would you rate your year on a scale from 1 to 10? 1 to 100? Why? Adding some context to your experiences presents a more accurate picture of your year by tempering unusual highs and lows.
Is my current daily routine structured to make time for my priorities?
It’s easy to fall victim to time suckers, especially when they become ingrained into your routine. Has your daily 15 minute coffee break gradually morphed into 25 minutes? Are your 10 minute “headline scans” now closer to 30 minutes? These small, seemingly innocent extensions can snowball into major time loss, causing unnecessary panic as you scramble to meet deadlines.
Try this: The start of a new year is a great time to reset (or rethink) our daily routines. Build activities into your day. If you’d like to continue your now-daily 25 minute coffee break, think about extending your work day by 25 minutes. Feeling like you can’t absorb everything news-worthy in less than 30 minutes? Set your morning alarm 30 minutes earlier so you can arrive to work having already completed your scan of daily headlines. By taking a hard look at where your time is actually going and then spending a few minutes realigning your daily routine with your priorities, you’re intentionally and consciously assigning time to the things you find the most important.
What is it that I want to achieve next year?
Each new year brings with it a renewed energy to being our best selves. In order to get started, we need to define our priorities and what our success will look like. Setting SMART goals, or goals that are specific, measurable, achievable, realistic, and timely, keeps us moving forward by providing accountability.
Try this: After reviewing your past year, set aside some time to consider what you’ll set out to achieve this year. Create a detailed roadmap to successful completion of your goals.
Use this infographic to help you set, and achieve your SMART goals.
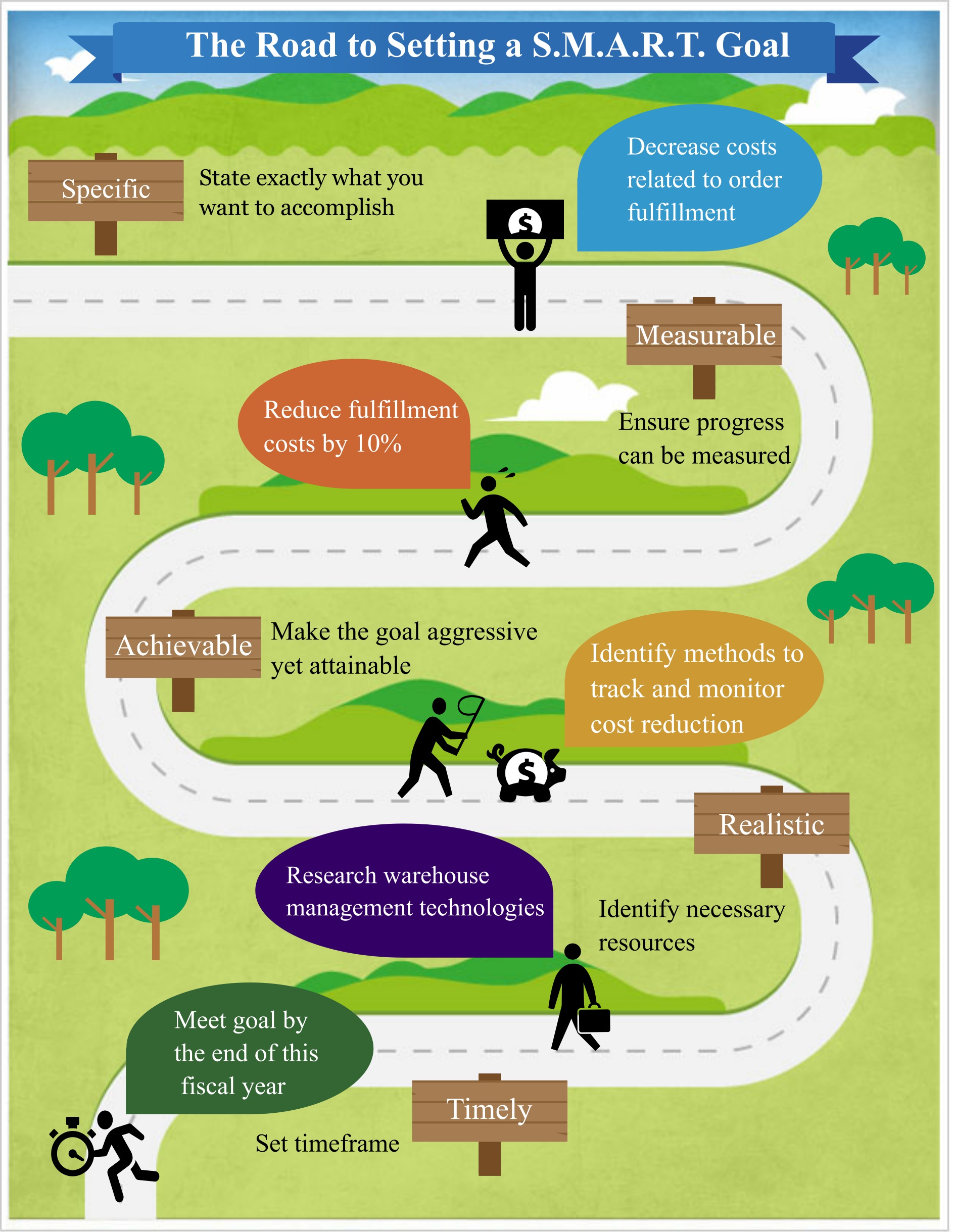
How was your year in review? What were your biggest accomplishments? Are there any goals that you’ll carry over into the new year? Do you regularly set aside time at the close of a year to reflect? We’d love to hear what you do to reset for a new year.
Fronetics Strategic Advisors is a leading management consulting firm. Our firm works with companies to identify and execute strategies for growth and value creation.
We advise and work with companies on their most critical issues and opportunities: strategy, marketing, organization, talent acquisition, performance management, and M&A support.
![How to Keep Your Company Data Safe in a BYOD Environment [Infographic]](https://fronetics.com/wp-content/uploads/2024/10/BYOD-policy-checklist-800x675.jpg)
by Fronetics | Sep 16, 2015 | Blog, Data Security, Data/Analytics, Marketing, Social Media, Strategy
While the Bring Your Own Device (BYOD) concept has quickly gained traction in the business world, many companies have been slow to address its threat to their data privacy. Even for companies that have recognized the need to prioritize digital security, many have struggled to establish policies that support personal device use while protecting their data. And that’s risky given the high level of connectedness many employees now enjoy – with or without formal guidelines or policies. It leaves businesses open to enormous potential for data leaks.
To avoid the potential leak of data, your company should establish policies on the use of personal and mobile devices such as tablets, smart phones, and laptops that may be used to access your company’s computing and communications systems. Here are six crucial items to consider as you set out to mitigate the risks of your own BYOD culture.


by Fronetics | Sep 15, 2015 | Blog, Data Security, Data/Analytics, Marketing, Social Media, Strategy

Personal connected devices – our laptops, cell phones, and tablets – are arguably the most complicit tools in the recent blurring of the parameters between personal and work life. And while most businesses have generally recognized the benefit of allowing employees to use their personal devices for work purposes, the bring-your-own-device (BYOD) revolution has certainly thrown a curve ball to those responsible for safeguarding company data. Although corporate finance groups are singing the praises of the trend due to its inherent reduction in costs, it’s not all rosy in the BYOD world. That’s why it’s crucial to format a corporate strategy policy that will protect your company from a potentially dangerous data-leak train wreck.
Here’s why: Employees are now widely accessing corporate data from their own computer, a tablet, even their mobile phone. With so many of us bringing more and more smart devices inside our office environments and hooking them to our corporate networks, the potential for data leakage grows exponentially. When anti-virus and digital security software company BitDefender set out to explore the connectedness of typical American workers last year, they found that over half stored work-related data on their personal devices. Shockingly, almost 40 percent of them had nothing in place to prevent unauthorized access to their device. Further, in a study conducted by the University of Glasgow, 63 percent of used smart devices purchased through second-hand stores and eBay-like marketplaces still had data on them. This data included personal information as well as sensitive business information.
The problem is there’s no chain of custody in the BYOD world. Think about it. When the corporations owned your cellphone and your PC or laptop, they controlled its issue to you, how you used it, what software you put on it, and when and how it was turned in and destroyed. A solid internal tracking of electronic assets coupled with a solid electronic asset disposal solution provider meant that, for the most part, the corporate digital assets were safe. In the BYOD world, the corporation does not own the IT equipment. Personal smart devices are being linked to corporate IT environments. This mating of personal and professional equipment and data is happening everywhere. Your corporate data is being commingled with secure and non-secure access points to the Web, cloud, etc. Not to mention the fact that those devices metaphorically walk in and out of your office every day, and you have no control.
Companies are scrambling to address this issue in a number of ways. Some have addressed the problem via software solutions at the enterprise level (think Blancco or BlackBerry enterprise), some at the device level (think solutions like Apple Find My Device, etc.), and some at the human resources and legal levels with policies and procedures that prohibit users’ use of corporate information. But the truth is, without a chain of custody model incorporated with these solutions, once the corporate data is accessed or downloaded, it’s already gone — you just don’t know it yet.
The reality is that it’s going to take some time for the corporate world to catch up with what some have called the “semi-private information revolution” like the cloud, Facebook, or social media. Secure file sharing, essential for an organization’s BYOD guidelines, is one of the best options available. Services are now available to help with cloud encryption and it’s changing the way we share and monitor files. Encrypting data is crucial and minimizes the risk of sharing sensitive data and having it tampered with. Rely on your electronic asset disposal provider to help your company develop a strategy and process that is aligned with your corporate information sharing guidelines. Right now, your corporate data is only as safe as the process that you create.
Fronetics Strategic Advisors is a leading management consulting firm. Our firm works with companies to identify and execute strategies for growth and value creation.
We advise and work with companies on their most critical issues and opportunities: strategy, marketing, organization, talent acquisition, performance management, and M&A support.
![Unlocking Your Marketing ROI with Analytics [infographic]](https://fronetics.com/wp-content/uploads/2024/10/Fronetics-Marketing-ROI-800x675.png)
by Fronetics | Sep 9, 2015 | Blog, Content Marketing, Data/Analytics, Marketing
In the age of big data, everything in marketing is measureable – and that’s not necessarily a good thing. As Dimitri Maex of Ogilvy Consulting puts it, “marketers are drowning in numbers because they are focused on what they can measure rather on what they should measure.” Unfocused efforts to evaluate the success of your marketing activities can lead to a host of problems. Central to these problems, though, is the failure to measure and report activities in a way that clearly demonstrates the link between marketing and your company’s bottom line. Check out our infographic that details four marketing metrics guaranteed to resonate with your CEO (and our guide to the 6 marketing metics your boss really cares about).

You might also be interested in:
When it comes to marketing we work with our clients to create and execute strategies that drive success and elevate their brand position within the industry. Unlike other firms, we align marketing programs with business objectives and, through a data driven approach, are able to deliver results with a targeted ROI. Our team is comprised of strategists, marketing professionals, writers, designers, and experts in social media. Together we leverage our experience to increase brand awareness, position our clients as thought leaders, drive meaningful engagement with prospects and customers, and help businesses grow.





![Supply Chain: 4 Essential Year End Questions to Ask Yourself [Infographic]](https://fronetics.com/wp-content/uploads/2024/10/supply-chain-year-end-questions-900x675.jpg)


![How to Keep Your Company Data Safe in a BYOD Environment [Infographic]](https://fronetics.com/wp-content/uploads/2024/10/BYOD-policy-checklist-800x675.jpg)



![Unlocking Your Marketing ROI with Analytics [infographic]](https://fronetics.com/wp-content/uploads/2024/10/Fronetics-Marketing-ROI-800x675.png)

